The Wiretap: China Has Infiltrated Police Wiretap Systems
Actors associated with the Chinese threat actor group tracked as Volt Typhoon accessed telecommunication systems that are utilized for lawful intercept, a feature that allows law enforcement with legal authorization to intercept communications, a requirement established by CALEA:
The Communications Assistance for Law Enforcement Act (CALEA) is a statute enacted by Congress in 1994 to require that telecommunications carriers and manufacturers of telecommunications equipment design their equipment, facilities, and services to ensure that they have the necessary surveillance capabilities to comply with legal requests for information.
This “backdoor as a feature” anti-pattern keeps rearing its ugly head, especially regarding special access given to law enforcement. When a backdoor is installed, you can’t be sure who is going to use it as we’ve seen over (tech companies) and over(ring doorbell) and over (Sony) and over (old web shell utilized by CISA red team).
I think telecom exploitation is likely to become a hot topic in the coming years as it’s a tangible example of a target that is digestible to the general public and regulators which will lead to regulations on the Telcom industry to increase security. Explaining the threat model of cloud environments to the general public is hard. Saying “adversaries are wiretapping you” is concise and a sentiment people can rally behind. Additionally, telco systems are not known to be the most secure products.
Zero Trust and Insider Threats
The 2024 Insider Threat Report paints a bleak picture of the rise of insider threats. Most of the report tracks statistics that show increases in risk from insiders (Note: The report is put together by two companies that sell products to “solve” this problem). There is likely some correlation between the increased risk from insiders and increase in polarization within the US. Architecting for security from unintentional threats (such as misconfigured services) is very different than architecting for security against an insider with malicious intentions (more on this later). It would be interesting to see data on the motivation behind intentional insider threat incidents.
It’s important to understand that many of the controls to protect against insider risk threats are also controls that organizations should be moving towards anyway – specifically, enforcing the principals of least privilege at scale which is the core idea behind Zero Trust Architecture (PDF). Notice that “at scale” is doing a lot of work in the previous statement, developing systems that allow your organization to easily and automatically enforce the desired state of security is the key to making sure these principles are enforced. If security relies on a human at any point, it has a chance of failing.
The best practices recommended in the report are:
- Implement Advanced Monitoring Solutions (Which the sponsor of the report happens to sell)
- Integrate Non-IT Data Sources
- Leverage Automated Threat Detection and Response
- Adopt a Zero Trust Framework
- Enhance Employee Training and Awareness
- Foster a Security-Conscious Culture
- Conduct Regular Security Audits and Assessments
- Implement Comprehensive Incident Response Plans
One gripe with this report is I did not see any definition for what constitutes an “Insider Attack” which I believe is very important to make clear. Side note: the reason we’re seeing a rise in these “year in review” style reports is that it establishes a great brand reputation for being a domain expert and works as a great purchase funnel. This can backfire quickly if the content of the report isn’t data-driven, transparent and obvious marketing. The problem isn’t limited to the security field either, even Spotify is facing backlash over their recent “year in review” Spotify wrapped feature for not distilling interesting insights from the data they collect.
From Me: Chasing The Ghost In The Wire
I recently read Staff Engineer and it got me thinking about where I spend my time. One concept that stuck out to me was ghost chasing. Ghost Chasing is a pattern of thinking where employees in new jobs/roles/environments chase ideas of high importance in the last job/role/environment they were in, not what is important for the current environment because the old problems are familiar and recognizable. Avoiding this is difficult, it’s hard to distinguish between experience and Ghost Chasing. A solution is to work on projects that are important but have not been approached yet, usually because it has complexities associated with them that make them unapproachable to most. This can take many forms:
- Red team: The problem – your company has inconsistent reports. Some are great, some are terrible. If you’ve seen this in the past, you might think to chase ghosts by attempting to give everyone a bigger training budget. A better solution might be to take on the arduous task of creating an SOP for each type of assessment and push leadership to allow having multiple testers on an engagement that can keep each other accountable.
- Blue Team: The problem – you’re inundated with low quality alerts. The solution that may be chasing ghosts is to play the endless game of alert tuning. A better solution might be to take on the responsibility of reaching out to infrastructure teams to work on getting logs from more critical locations allowing higher-quality detections to be crafted.
- CISO: The problem – everything is on fire and your budget isn’t unlimited. The solution that may be chasing ghosts is to distribute the budget so the majority of the budget goes to the most at risk projects. A better solution might be to hire experts who can help determine which security controls, if implemented correctly, fix a disproportionate amount of the issues across all teams.
Caught My Eye
- Supplychain Firewall: An open source project from Datadog that can help developers protect themselves from downloading malicious or vulnerable software packages from
pipandnpm. The workflow is relatively simple. Instead of runningnpm install <package_name, developers can instead runscfw run npm install <package_name>which queries Data Dog’s public dataset of malicious PyPI or npm packages as well as open source or custom, user-defined, data sources. An example from the project’s GitHub page:
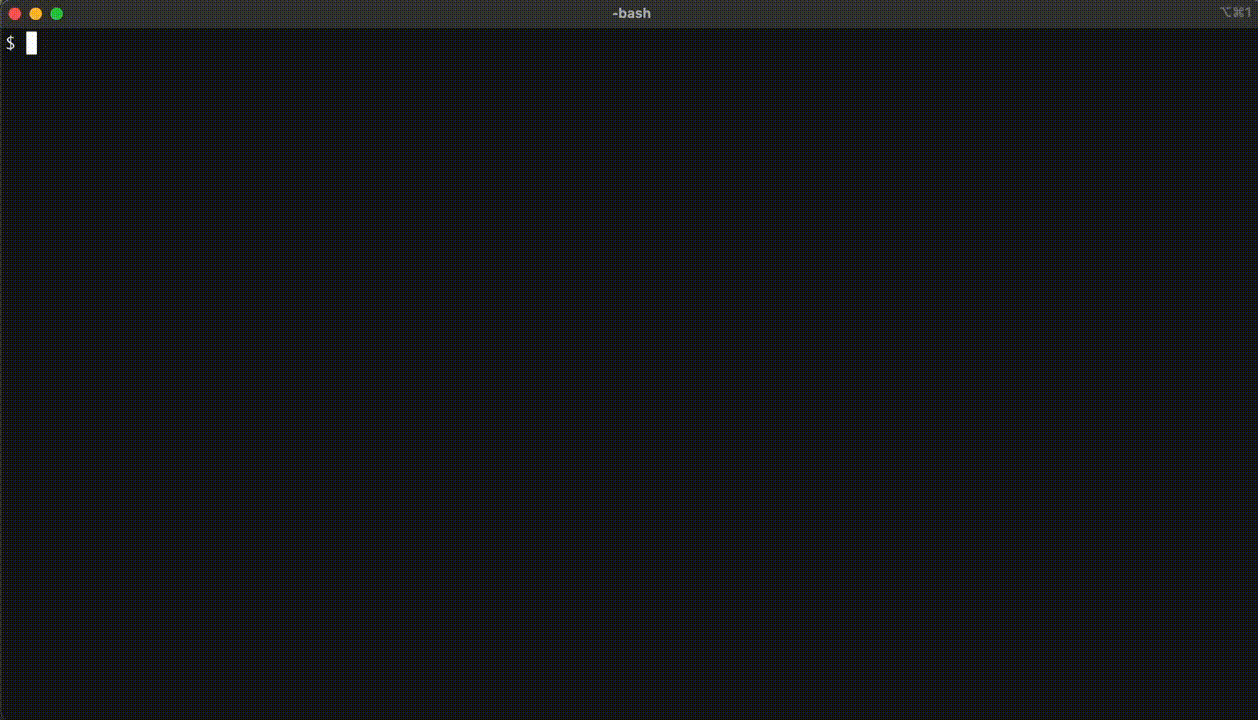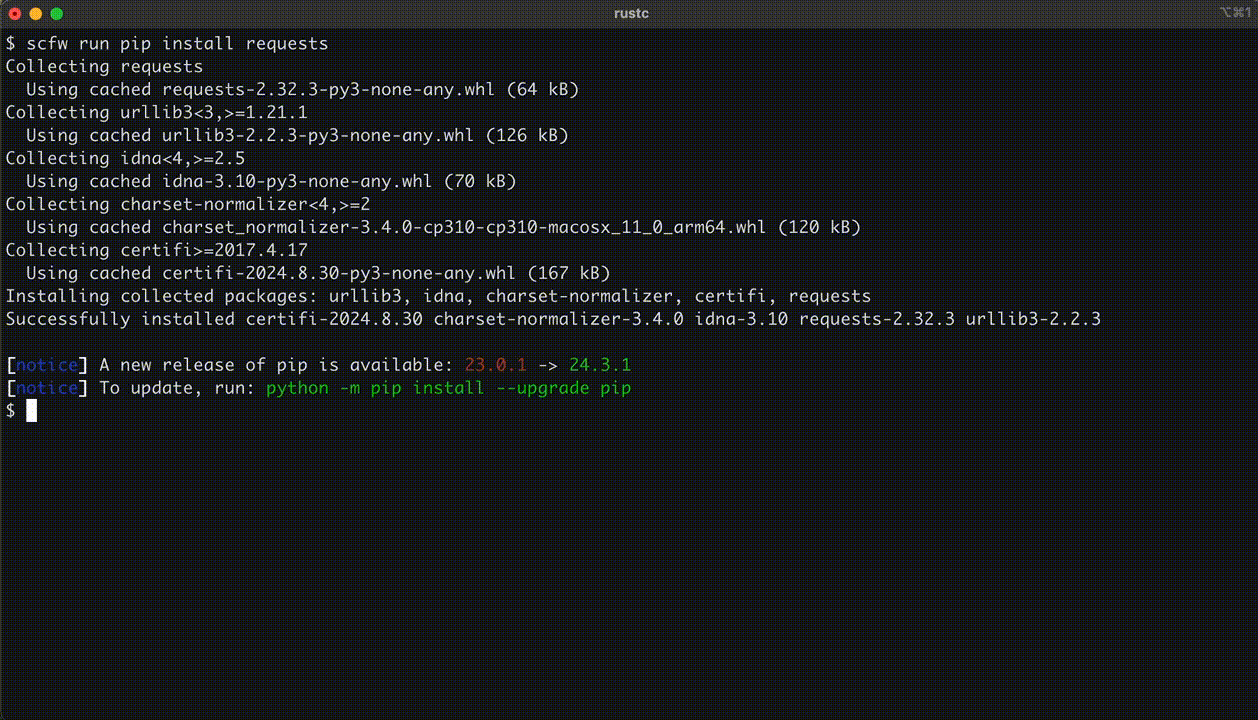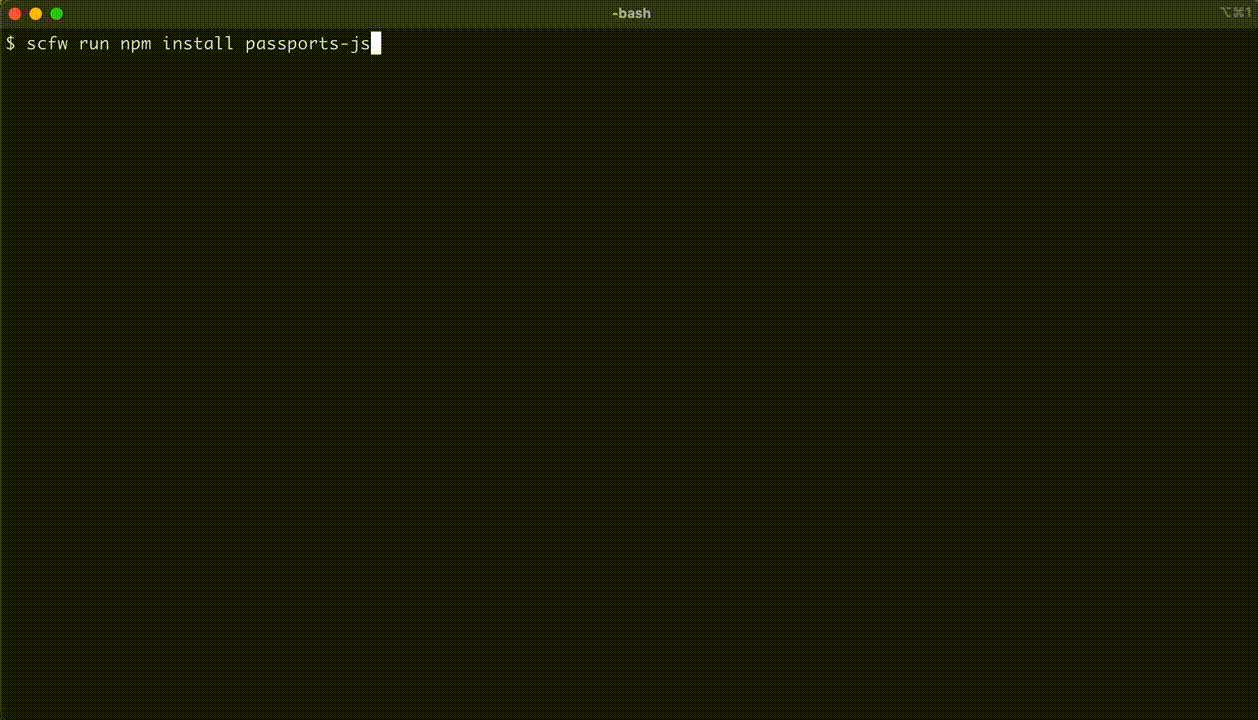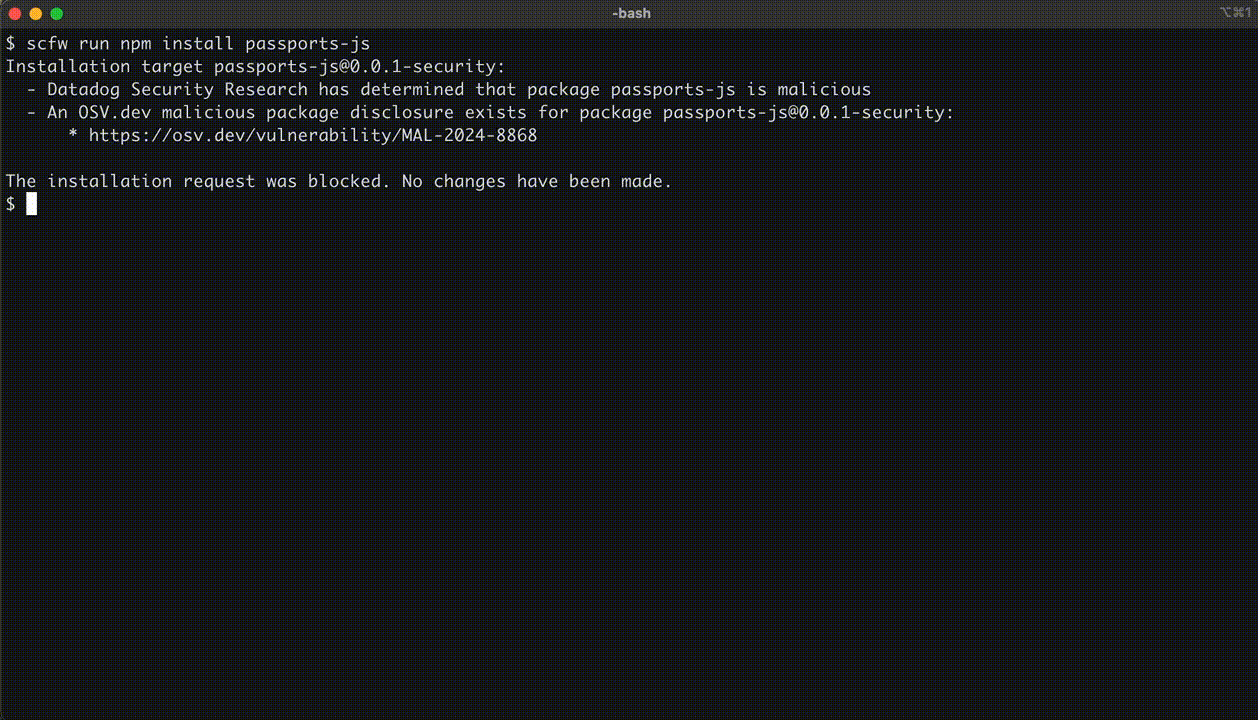
- urlfinder: Short and simple, URLfinder passively gathers URLs associated with a domain. I always love the projects from ProjectDiscovery.
- Group Policy Nightmares: A great writeup of a not-so-obviously bad group policy options.
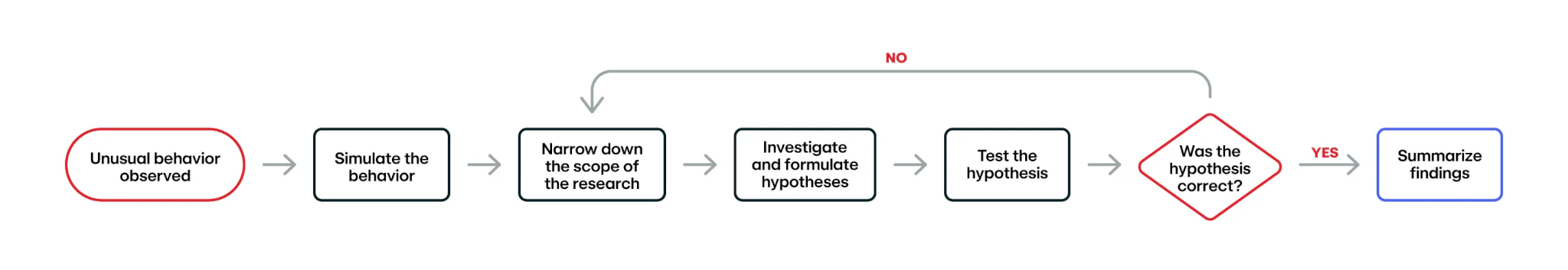
- The Dark Cloud Around GCP Service Accounts: While this has some interesting insights around GCP service accounts, this post is really insightful on how to perform security research. Put visually, this is the process of performing security research:
- Demystifying ASLR: Understanding, Exploiting, and Defending Against Memory Randomization: A great basic-intermediate overview of ASLR. Side note: If you’re publishing a technical blog, I highly recommend not hosting it on Medium. Part of the power of a blog is to increase your personal brand – hosting it on Medium makes it difficult to distinguish your work from others since they’re all the same branding.
- TrustedSec On-Demand BOF Training: TrustedSec has released a new course on Beacon Object Files. This is the shift I was talking about in my post about Federated Security Training
- Go Modules and packages – which one to use and when: A nice explanation of Go modules and packages, I’ve found this to be a confusing area in the past.
- The Pedantic Distinction Between RCE and Command Injection: TLDR; Abusing existing privileges != remote code execution.
- Staying Professionally Detached From Your Security Research: This article touches on the unfortunate toxic culture often associated with reporting security findings.
- Credit Card CanaryTokens. Another fantastic feature from thinkst. Put a canary credit card somewhere and get alerted if it’s ever used.
- Hacking2024 Humble Bundle: Humble bundle has a bundle of cyber-security books available. I’d wager that reading these books will give you more context about how security works than nearly any 4-year degree. Proceeds go to the EFF and ACLU