2024 CISO Compensation Report
IANS released the 2024 CISO compensation report in October and while I recommend reading through it (especially if this is the world you are in) here are the main compensation numbers: $403k (Median), $565k (Average), $1.02M (Top 10%). There is nothing too surprising here, CISOs make a lot of money. The recommendations for increasing value and pay are:
- Align the security program with business objectives
- Build strong relationships with the leadership team and board of directors
This is difficult, but being able to craft a story to brief leadership can go a long way to build trust. One way to do so is monitor then news for highly public breaches, identify the TTPs used, map them to MITRE attack, and then either hire someone externally (or preferably have someone already on staff) to test each of those TTPs. If you have multiple defenses for each attack. Craft the story around how the money being spent on security is helping protect the business and enabling it to grow safely. Here are some of the more interesting data points that stuck out to me:
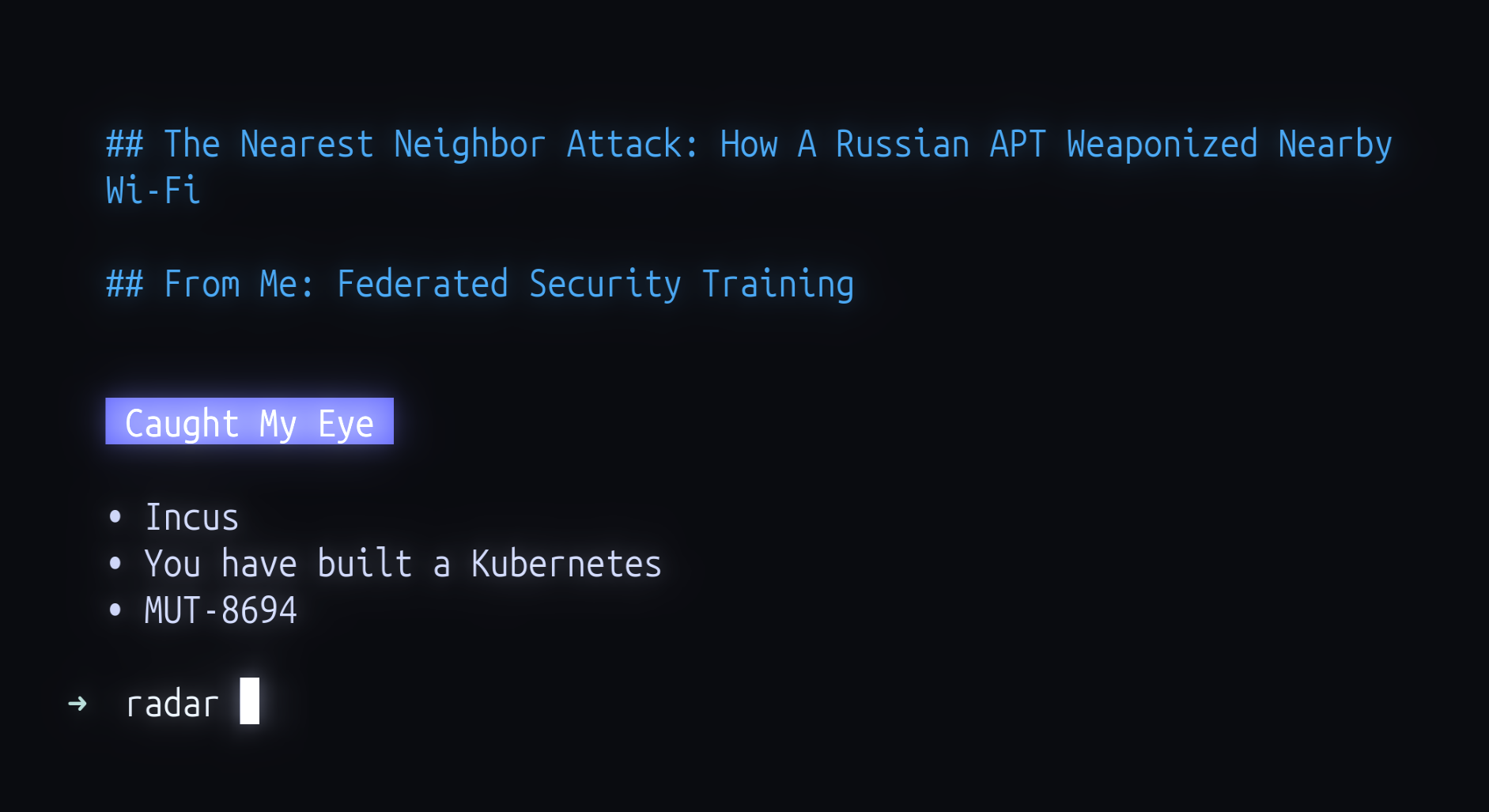
- Total Compensation by Sector: To no one’s surprise, Tech and Financial services are the top-paying positions. It’s interesting that the Healthcare and Hospital sectors (which are listed as different categories in the report) are significantly lower paid on average than those in tech, financial services, and consumer goods. This is a good reminder that compensation is not a good metric for how hard your job is. I doubt any of the sectors in top-paid sectors work any harder than those in the least-paid sectors.
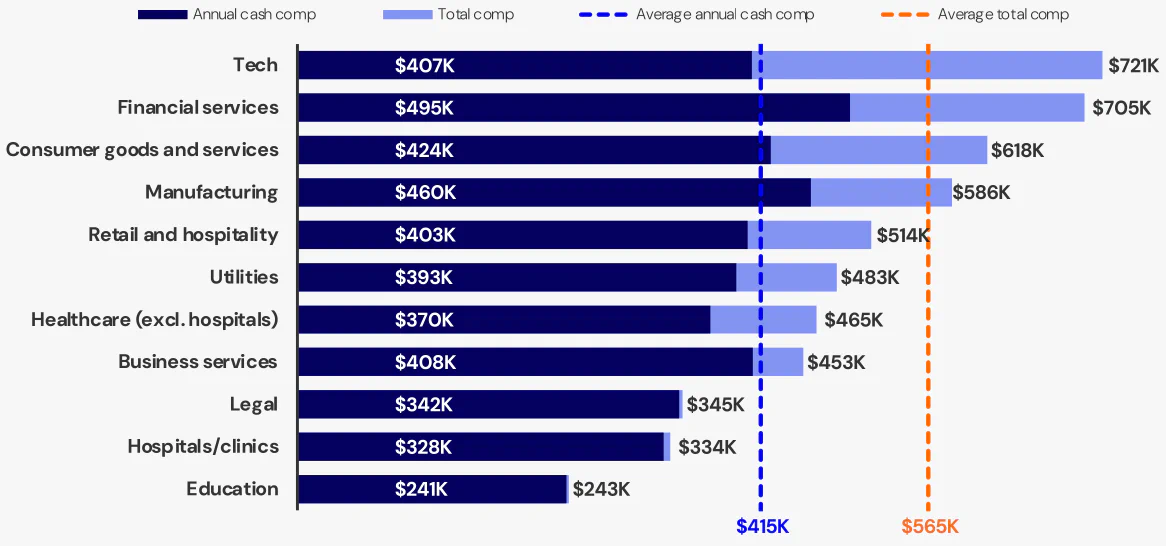
2 . Regional Differences in CISO Compensation: This figure is fascinating. The total comps in areas such as San Francisco and New York make sense and play a role in raising the average compensation of these areas. Interestingly, the Southeast has a lower total compensation than the Central US which is surprising. I’m also shocked to see Canada’s total compensation significantly lower than even the lowest regions of the US.
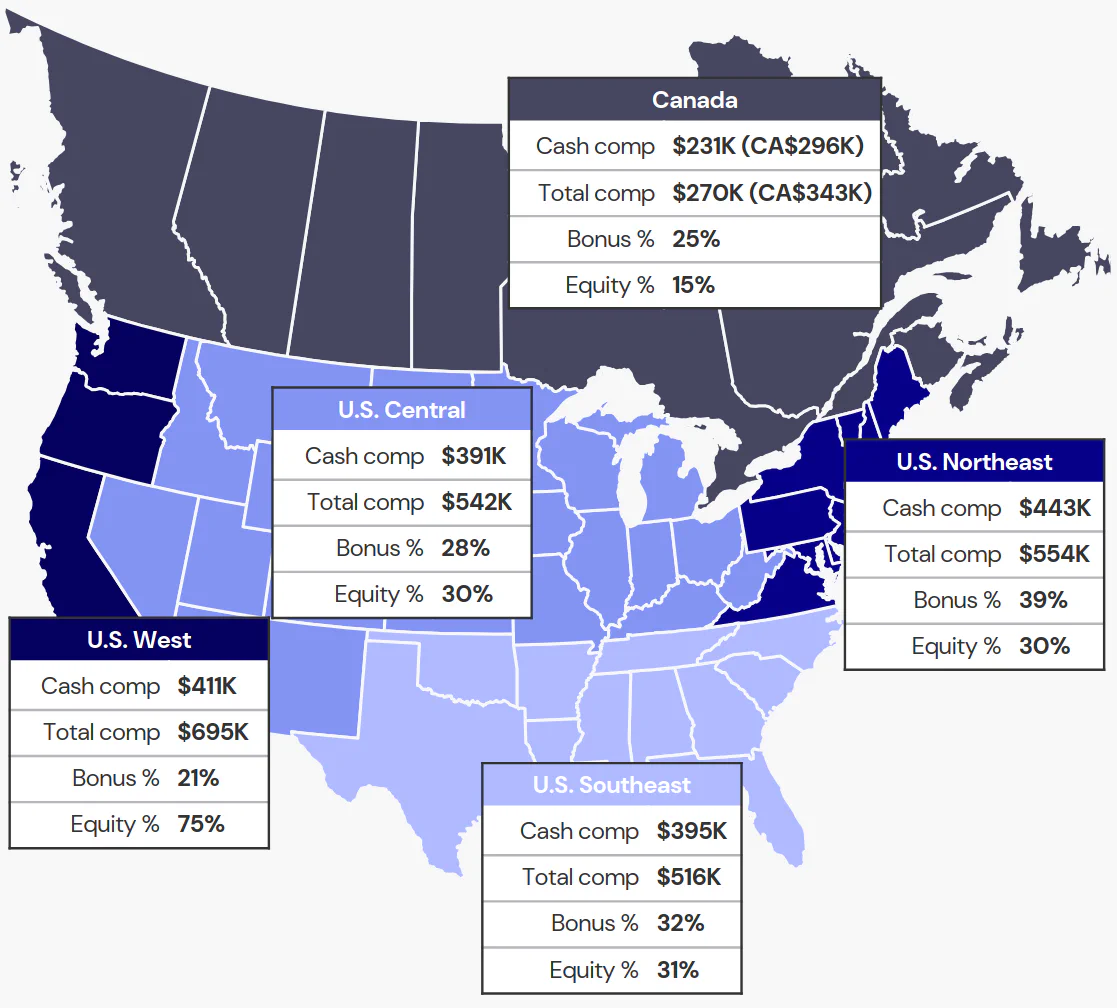
- CISO Compensation Satisfaction: Turns out, not getting an increase in compensation makes CISOs more dissatisfied with their compensation, who would have guessed? According to just these numbers, even for C-level employees, changing jobs is still the “best” way to increase your satisfaction with your compensation. This is very true and well-documented, especially in the tech industry. Offering a one-time bonus or promotion also greatly increases compensation satisfaction. I wish there was data on the dollar amount of the bonus.
The Nearest Neighbor Attack: How A Russian APT Weaponized Nearby Wi-Fi Networks for Covert Access
The nearest neighbor attack is an interesting story of how OrgA was compromised through a highly targeted attack that relied on the threat actor getting access to the neighboring company’s network (OrgB) and using a WiFi adapter in OrgB to connect to OrgA’s resources that were not protected by MFA if connecting via WiFi. Of note, OrgB seemed to have been compromised in the same way from a different neighboring company. The reason this level of sophistication was needed was that all public-facing assets required MFA, which the attacker did not have access to. They were able to obtain multiple valid passwords for OrgA users by spraying them at the public-facing assets. While they couldn’t log in using it over the internet, it tipped the threat actor off that the credentials were valid and they could be used if authenticating via the WiFi.
I have not tested it, but I wonder if some sort of detection when a user authenticates with a valid password, but never completes the 2nd factor. While this is a super interesting attack, it’s not something most companies need to have as their top priority. Some takeaways are: Log as much as you possibly can and what risks are you willing to accept? Was the risk of being attacked over WiFi deemed too low? Was it even identified as a risk?
From Me: Federated Security Training
Historically, training/education was centralized. You had to go to a certain school or company to obtain a degree or professional certification. While (for the most part), companies hiring for security roles have realized that a degree doesn’t mean much in terms of competence, we still heavily over-value certifications over aptitude. I’ve talked extensively about this issue on the demand side – addressing what you can do to stand out in your industry. On the supply side, I think we’re about to see (or are already seeing?) a massive increase in the amount of training being offered by individual companies or professionals, especially with highly respected instructors (See: Here and Here) leaving traditional training companies in droves.
This “Federated Security Training” model makes a lot of sense to me – the cost will be lower because it goes straight to the instructors and the quality will be more relevant because it can be updated quicker. The cons? Word-of-mouth marketing and a good instructor reputation will be super important. You may also be concerned about the lack of certifications approved by a “certifying body” for this training, you shouldn’t be though, we should probably move away from certification-based competence. What does this mean for you?
- If you’re looking for good training, look beyond the traditional players.
- If you’re hiring, having a network of people you would like to hire is more important than ever. Let’s be honest, the chance of HR passing you a solid resume is much lower than meeting someone at a conference with a solid resume.
- If you’re looking to advance in your career, take the knowledge you’ve obtained and create a reasonably priced training is a great way to demonstrate your domain expertise advance your career, and make great connections to those interested in the same topic.
Caught My Eye
- Incus: This is a VERY interesting project. Essentially, Incus is a container and VM manager with a very minimal yet clean web interface. If you’ve worked with something like Proxmox or ESXi, you’ll feel right at home in the web UI but you can also directly launch VMs/containers from the command line interface. Very interesting. There is a free demo instance that can be used to explore the functionality.
- You have built a Kubernetes: A humorous dig at those that bemoan the complexities of Kubernetes by proudly brandishing their unhinged directory of bash scripts and Ansible playbooks.
- MUT-8694: An NPM and PyPI Malicious Campaign Targeting Windows Users: Your typical malicious packages being introduced, interestingly this was target both npm (JavaScript) and PyPi (Python) package repositories. I continue to be impressed with Datadog’s security research.
- Cloud-Security-VM: Ansible/Vagrant/Packer files to create VMs with cloud security assessment tooling built in. I continue to find the most time-consuming part of security is getting the infrastructure setup. A good habit to develop is creating a list of “things that can be automated”. Whenever you get free time, work on that list so that in the future you’ll have to spend less time working on repetitive tasks.
- ogSec Code Review & Architecture Fundamentals: A course on code review I’m thinking of going through soon.
- Infosec Black Friday Deals: Some goodies in here. Most end on November 30th, 2024
- PAGED OUT! (PDF): A fantastic magazine with deeply technical content. I recommend “Circumventing Disabled SSH Port-Forwarding with a Multiplexer” and “Execve(2)-less dropper to annoy security engineers”.