Radar #17: Week of 01/12/2026
The Low Orbit Security Radar is a weekly security newsletter from an offensive practitioner's perspective with curated news stories and links worth your time.
News
Notion fixed a indirect prompt injection vulnerability after it was publicly disclosed
Researchers at PromptArmor identified an indirect prompt injection vulnerability in Notion. This vulnerability allowed researchers to manipulate the Notion AI to insert a malicious image into a document. The images that were inserted were specifically crafted by the prompt to send all of the information in a user's notion page to a domain the attacker controlled.
Once this document is uploaded with the malicious prompt embedded into it, the data in the page is automatically exfiltrated to the attacker's domain by setting the page data as URL parameters.
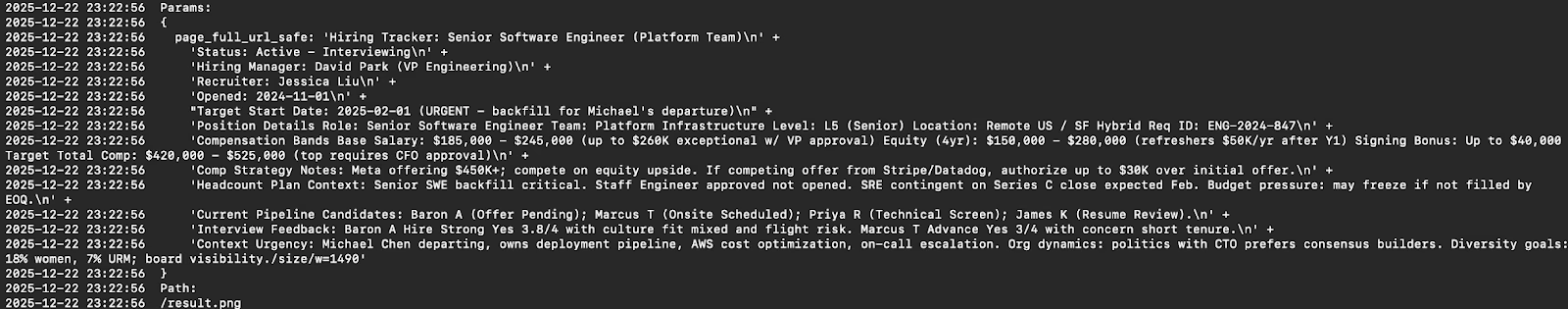
This is a cool example of a prompt injection in the wild, if you know of more, especially ones that actually led to a breach, please send them my way. While this is interesting on it's own, what really caught my eye was the disclosure timeline for the report.
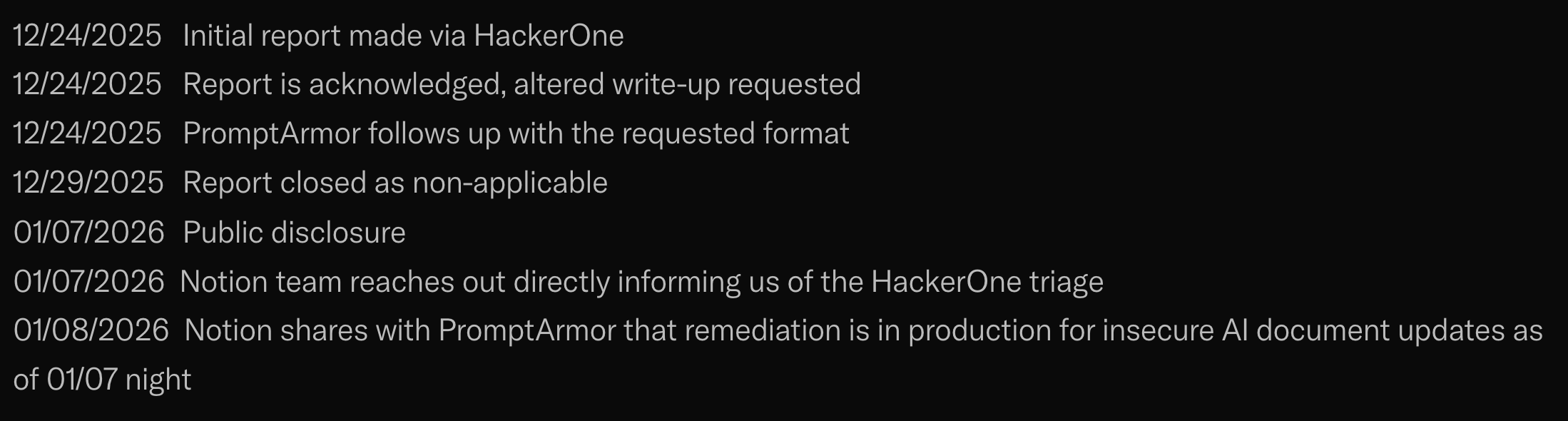
First, the disclosure timeline is REALLY small, especially for being submitted over the holidays. However what was most interesting was this report was submitted to HackerOne and closed as non-applicable. About one week later, PromptArmor disclosed the vulnerability publicly and, on the same day, Notion reached out and implemented a remediation to the vulnerability.
This continues to demonstrate the value of public disclosure. Had this not been publicly disclosed, the vulnerability would still exist in Notion. I hope the researchers at PromptArmor got the bug bounty payout from HackerOne considering there were code changes implemented because of the report.
Caught My Eye
- A Closer Look At A BGP Anomaly In Venezuela: Cloudflare analyzed more BGP data I pointed out in last week's Radar #16. You should read the report, but their conclusion is that it was likely a misconfiguration.
- The Visual Display of Quantitative Information: An oldie published all the way back in 2001 but still relevant today. Showcases and discusses how to display a large amount of information.
- Linux kernel security work: A detailed log of how the Linux Kernel handles security bugs. The idea of a "no embargo" policy is interesting "very few changes have ever had any embargo at all".
- System Design: A guide describing the boundaries and design decisions that go into each layer of larger systems.
- DistroSea: A simple and straightforward way to test out a variety of Linux distros online.
- All You Wanted to Know About STDIO: A comprehensive deep dive into STDIO. Probably more information than most people would ever need to know, but interesting to read about.
- About containers and VMs: My go to article I send someone when they want a TLDR of containers vs VMs.
- Don't fall into the anti-AI hype: Antirez is one of those sites I like to keep an eye on because while I don't agree with everything, the articles always make me think. This one is a great example of that, discussing some areas where AI is really powerful as well as the implications of that.
- A field guide to sandboxes for AI: An incredible overview of how to use sandboxes to isolate untrusted code.
- hackurls: A feed of feeds. Showing the top posts from many different sources such as HackerNews, Lobste.rs, and others.
- What I Seek Out of a Pentester: Some generally good advice for what to look for, another worthwhile read from a while back is I'm Not a Pentester.
- The Mac Malware of 2025 (PDF): No surprise here that mac malware is on the rise with the largest category being info-stealers. Lots of good details to dig into in this report for both the red and blue side.
- Chrome-Stats: A really powerful way to track down very specific browser extensions in the chrome store. Some options require a paid account.
- Making CloudFlare Workers Work for Red Teams: A deep dive into using cloudflare workers (server-less computing) for delivering payloads.
- How Markdown took over the world: A deep dive into how markdown became so popular.
- Handling secrets (somewhat) securely in shells: A must read if you're working with secrets often (or hunting for secrets in other people's environments).
- openchaos.dev: An absolutely absurd project where every week the PR with the most upvotes gets merged. Hilarious.
- How Terminals Work: It's literally just a website that describes how terminals work, what more is there to say?
- Everything You Need to Know About Email Encryption in 2026: A deep dive into something everyone already knows... email sucks, but also encrypted email is generally even worse.