The Low Orbit Security Radar is a weekly security newsletter from an offensive practitioner's perspective. One idea, curated news, and links worth your time.
This Week
$ radar --status
SIGNAL: REACQUIRED
LAST_TX: 01/27/2025
STATUS: OPERATIONAL
[Low Orbit Radar, back online]
We've had a gap in transmissions. Some housekeeping before we resume.
- The Low Orbit Radar is back. Monday mornings.
- Low Orbit Radar Issues will take the following format.
# Radar #X: Week of MM/DD/YYYY
## This Week [2-4 paragraphs]
One observation, technique, or idea worth sharing. 2-4 paragraphs.
## News [1-2 paragraphs]
News items worth paying attention to, with brief analysis.
## Caught My Eye [0-n links]
Links that earned a bookmark.
- The content will continue to be an analysis of the security industry from my offensive security perspective.
News
Don't directly navigate to websites, use dashboards
A decade ago, ~5% of parked domain visits led to malicious content. Now it's over 90%. These "parked" domains are collected by "investors" called "domainers" and often serve ads to collect passive income to pay for their domain renewals.
Infoblox published an incredible investigation into what really happens when visiting these seemingly benign pages and uncovered a complex web of how a single mistyped url can lead to sketchy results at best and malware at worst.
Interestingly, the actor is using double fast flux on the domains which rotates both the IP and DNS nameservers making it difficult to track, block, and detect.
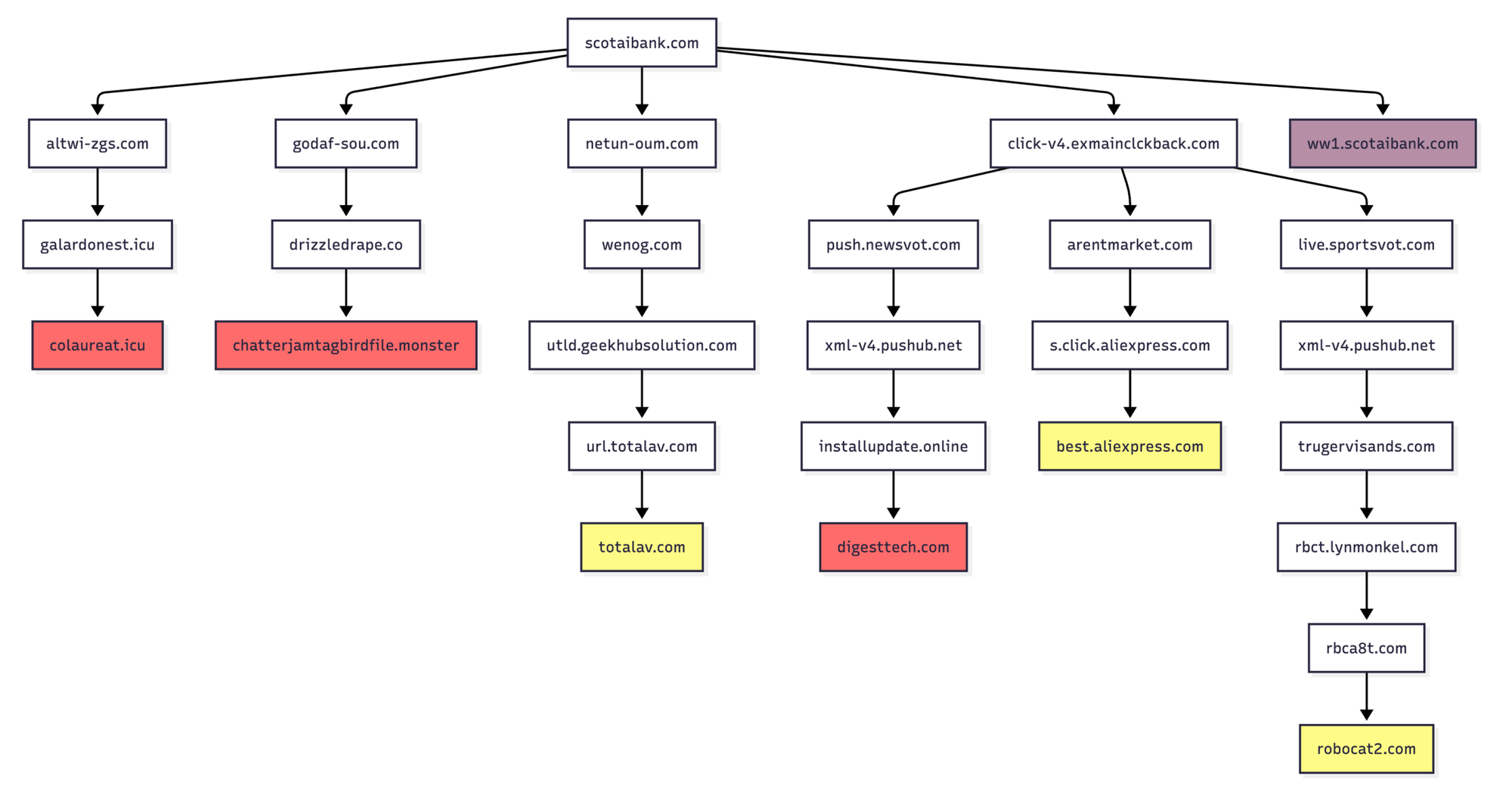
Parked domains being used for malicious purposes isn't new, but the scale is daunting. You can check for common variations of a domain using dnstwist. I know that typing a domain you visit often is second nature, but utilizing personal dashboards such as Glance is probably wise. Organizations should consider having an internal dashboard with common links.
Caught My Eye
- THC Subdomain Enumeration Tool Subdomain enumeration tools are cool, but what really caught my eye was the datasets are available for download monthly, great for offline recon.
- KubeCon + CloudNativeCon NA 2025 End User Summit Report: Engaging with AI: It's interesting to see the "pain points" being brought up about AI integration are business problems such as measuring ROI, not technical ones.
- Zero-Days in the Age of AI: Behind the Scenes of ZeroDay.cloud 2025: Wiz put on a competition for vulnerability researchers to pick a target and demonstrate it live on stage for a large payout. Vulns were found in the Linux Kernel, PostgreSQL, Redis, MariaDB, and Grafana.
- Meet exe.dev, modern VMs: Subscription service that gives access to VMs on demand sub second start, persistent disks, and some other quality of life features. Currently you can spin up VMs for free... in the words of a colleague: "A collocated redirector, just not one to burn tradecraft in."
- Careless Whisper: Exploiting Silent Delivery Receipts to Monitor Users on Mobile Instant Messengers: A technique that allows threat actors to roughly estimate when your phone is in use by conducting a timing analysis of packets sent to Whatsapp and Signal with a POC Available
- File d'attente - file-based job queue: A file-based job queue. Create a job by adding a file to
/pendingdirectory, and it will auto retry to execute it. Lightweight but has some interesting use cases. - D-Bus is a disgrace to the Linux Desktop: My 2 week adventure into D-Bus made me slightly concerned about how weird the D-Bus system is in Linux, this post does a great job at outlining its quirks. A great place to look for fun vulns.
- KubeVirt Security Audit Report: KubeVirt allows running virtual machines in Kubernetes, the Arbitrary Host File Read and Write is interesting... If you're auditing something, always look at mounts and/or symlinks, they're a goldmine.